Kek mano systemctl baco konpig pail?
list all service
$ systemctl -a | grep "myservice"
$ systemctl show "mycervice" | grep -i path
list all service
$ systemctl -a | grep "myservice"
$ systemctl show "mycervice" | grep -i path
# vmware-mount -p .vmdk
Nr Start Size Type Id Sytem
-- ---------- ---------- ---- -- ------------------------
1 63 401562 BIOS 83 Linux
2 401625 10072755 BIOS 8E Unknown # vmware-mount -f .vmdk
# ls
flat # fdisk -lu /mnt/ROOT/flat
You can do this from the extra functions menu.
Disk /mnt/ROOT/flat: 0 MB, 0 bytes
255 heads, 63 sectors/track, 0 cylinders, total 0 sectors
Units = sectors of 1 * 512 = 512 bytes
Disk identifier: 0x0006a266
Device Boot Start End Blocks Id System
/mnt/ROOT/flat1 * 63 401624 200781 83 Linux
/mnt/ROOT/flat2 401625 10474379 5036377+ 8e Linux LVM# losetup -o 205632000 /dev/loop0 /flat # pvdisplay /dev/loop0
--- Physical volume ---
PV Name /dev/loop0
VG Name VolGroup00
PV Size 4,80 GB / not usable 22,34 MB
Allocatable yes
PE Size (KByte) 32768
Total PE 153
Free PE 1
Allocated PE 152
PV UUID MUKx5v-ukpq-fJis-GjpB-Z7dE-nIsI-Xr4bYd# lvscan
ACTIVE '/dev/vg1/isos' [111,79 GB] inherit
ACTIVE '/dev/vg0/root' [10,00 GB] inherit
ACTIVE '/dev/vg0/swap' [8,00 GB] inherit
ACTIVE '/dev/vg0/home' [50,00 GB] inherit
ACTIVE '/dev/vg0/data' [164,41 GB] inherit
inactive '/dev/VolGroup00/LogVol00' [4,00 GB] inherit
inactive '/dev/VolGroup00/LogVol01' [768,00 MB] inherit# lvchange -an /dev/VolGroup00/LogVol00# losetup -d /dev/loop0# vmware-mount -d 
# ps aux|grep subl
root 3018 2.2 1.0 289008
61872 ? Ds 12:30 5:27 /opt/sublime_text/sublime_text D in the STAT column means it's in an in "Uninterruptible sleep". That usually translates to something waiting for an IO command. These cannot be interrupted by kill.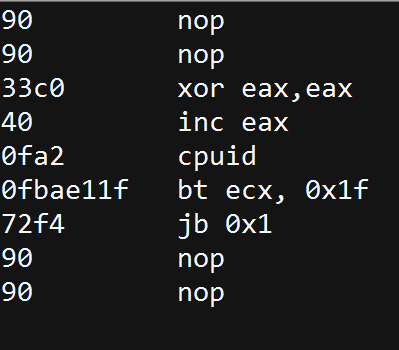
gsettings set org.gnome.shell.app-switcher current-workspace-only true